Creating an SSH connection using password authentication
SSH is a secure shell command line technology allowing a user to connect to a second computer and perform many tasks securely. I have written a post which is found here which tells out all about the SSH technology. In this post I am showing you how to connect to a SSH server in Windows and Linux operating systems using password authentication, if you are using public/private key authentication please read this post. I would recommend everyone to use public/private key authentication because it increases security dramatically, a SSH client can on connect to the server if they have the correct private key and a private key can be encrypted using a password increasing security even further.
SSH using Windows
SSH using Linux
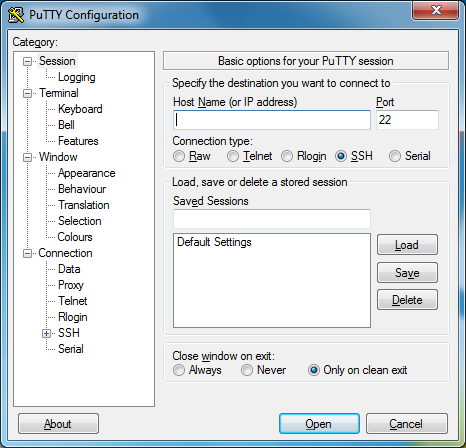
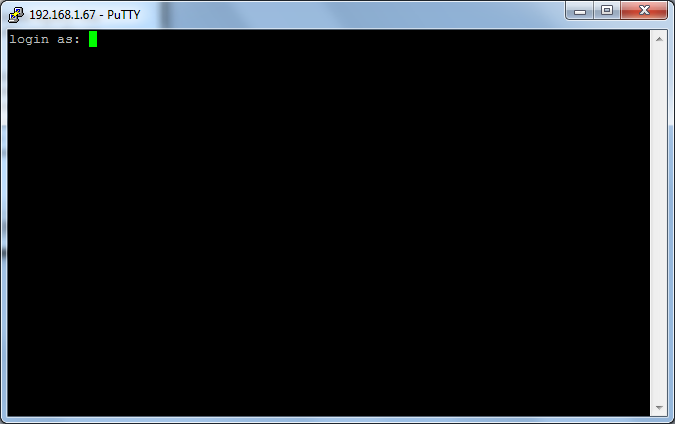
To allow us to perform SSH communications we need to download a SSH client which allows us to transmit and understand responses, the software we are going to be using is called PuTTy which can be found here, a direct link to the download required is here. Please download the file to an easy to find location such as the desktop. Once the file has been downloaded you simply double click it and it will launch, there is no need for any installation of this program. You will now have a window which looks like this.
PuTTy has allot of features which we won’t be going into just now and I will be writing more blog posts about these other features later, for this guide we are concentrating on connecting to a second computer securely using SSH. There are two fields on this page which we are interested in and that is the textboxes located at the top of the application labelled “Host name (or IP address” and “Port”, we need to provide the IP address (can also provide a hostname if it resolves to the correct IP address) and the port number which the remote SSH server (located on the second computer) is running on by default this is 22 but can be changed.
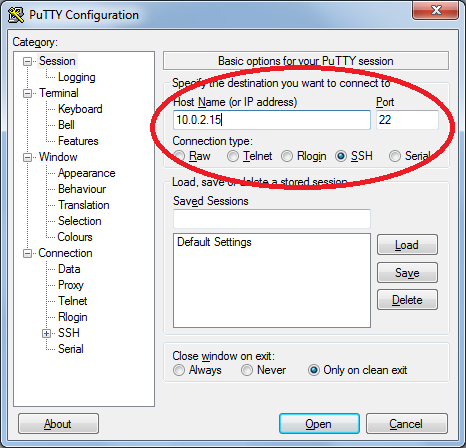
As you can see from the image above I have provided the IP address of the second computer and a port number of 22, the computer I am connecting to has a IP address of 10.0.2.15 and the SSH server is listening on port 22 for connections. Please enter the IP address or hostname of your second computer and the port number (most probably 22) and click the Open button located at the bottom of the application.
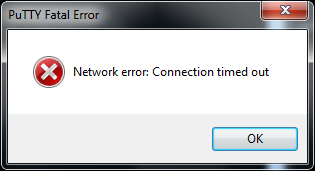
You may receive an error message like the one above, this means it failed to gain a connection to the second computer and there are many causes of this error. First thing would to make sure the SSH server is running on the second computer and the port is allowed on the firewall, next step would be to check that you have entered the correct IP address or hostname and port number and retry.
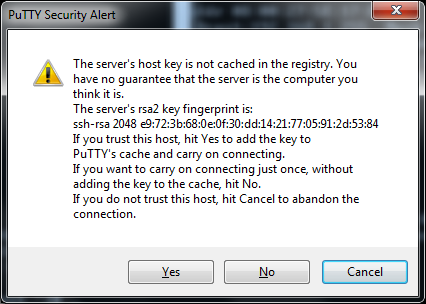
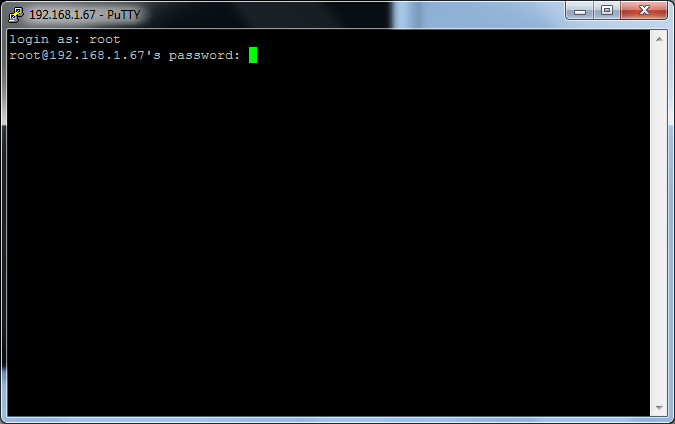
On a successful connection to the second computer through SSH you will receive an alert similar to the one above. This key is a way to identify that the second computer is who it says it is, you don’t really have to pay any attention to this and so I normally just click the yes or no option. If you click Yes this key will be saved for further usage stopping this alert from appearing every time you try to connect to this computer, clicking No will allow you to connect but will not save for further usage meaning it will appear again on the next login and cancel will stop the connection to the second machine. Now we are beginning the login progress where we need to enter the username of the user we want to login and then the password for that user. Simply type the username and press the enter key.
After pressing enter it will go to a line like the image below, now you type the password for the user you entered earlier. It may appear that nothing is being typed but it is, this is a security feature so that if people are watching they can’t see how many characters are in your password, press enter and you will login, now you can perform your tasks on the second computer.
If you do not receive a password entry field but instead receive a error message saying something along the lines of “No supported authentication method available” then the SSH server has password authentication disabled, this is to increase security as now a user can only connect if they provide a key which is normally stored in a file, this key is different for every user and is needed to be able to login.
Please read this post for instructions on how to use a private key to login using SSH.
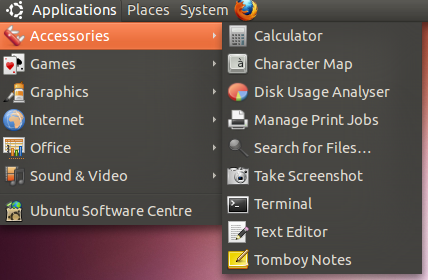
Unlike windows operating systems Linux has the ability to communicate with a SSH server straight after installation of the operating system (no third party software is required). I am going to be using Ubuntu operating system but this will work on all distributions of Linux. First we need to launch the terminal which is a command line interface which will allow us to perform the SSH login. On Ubuntu this can be found by going to Applications then accessories. You will be presented with a black window with some white text.
To start an SSH connection we have to type a command to begin the SSH software, we also have to specify the port which the SSH server we are trying to connect to is listening on (normally 22), we also have to specify the IP address or hostname and the user we wish to login with (if not user is specified it will try to login with the user we are logged in with on are client), the command to do this looks like this.
|
1 |
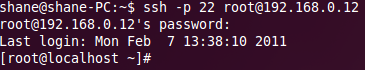
ssh –p 22 root@192.168.0.12 |
What this command will do is start a SSH connection to the SSH server running on the computer using the IP address 192.168.0.12 and listening on port 22, it will attempt to login with the user root. We can change the port we are connecting to by changing –p 22 to –p 2290, the SSH server must be listening on the port for it to be successful. We specify the user we want to login by placing the username then an @ symbol before the IP or hostname of the computer we wish to connect to.
|
1 |
ssh –p 2290 bob@192.168.0.12 |
The command above is another example where we are connecting to the computer which is used IP address 192.168.0.12 with the user bob. The SSH server is listening on 2290 instead of 22 so we specify the port number. If you are connecting to a SSH server which is using the default port (22) then you do not need to provide the –p argument, you can use the following command and it will automatically try connecting to port 22.
|
1 |
ssh bob@192.168.0.12 |
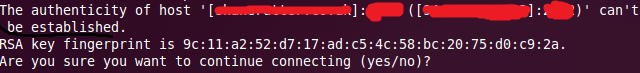
On connection you may be presented with a message like this and you are asked if you want to continue connecting. This is normal and allows you to determine if you are connecting to the correct computer or if someone is tricking you into connecting to them so they can intercept your data, every SSH server has a RSA key which you should write down on installation of the SSH server. You can then compare this key to the key which you are being shown on the SSH client, if they match you are connecting to the correct computer, if not then it’s possible someone has tricked you into connecting to them allowing them to view any data you transmit. You should enter yes if you are sure you are connecting to the correct computer, if you enter no it will cancel all communication.
On entering yes the RSA key will be saved permanently on your computer stopping this message appearing the next time you connect using SSH to this computer. If the key changes at all another message will appear alerting you to a key change, if you haven’t reinstalled the SSH server then the key shouldn’t have changed meaning there’s a high possibility someone has tricked your SSH client into connecting to them instead of your desired computer. You should halt all communication in the event of this message unless you are sure it is safe.
You will now have to enter the password for the user you wish to login with, when you type your password nothing will appear but it is typing, this is a secure feature so that people can’t see how many characters are in your password.
If you receive a error message like the one below instead of a password prompt then password authentication is disabled on the SSH server, this increases the security as now a user can only connect if they provide a key which is normally stored in a file, this key is different for every user and is needed to be able to login.
Please read this post for instructions on how to use a private key to login using SSH. To cancel out of a SSH connection you can type exit to disconnect.