What is SSH (secure shell)?
SSH short for secure shell is a network protocol allowing communications between two computers, it is natively found on Linux based operating systems and used to remotely control computers and server via a command line interface. SSH was created to replace older insecure software such as telnet, telnet lacked encryption allowing anyone to intercept the data transfer. For example it was possible someone could steal the username and password used which would give them remote access to the system.
SSH fixes this problem by creating a secure connection to the remote computer before any data is sent and received, once this encrypted connect was successful, login details such as username and password will be transmitted making it safe for use on insecure networks such as the internet.
The Advanced Features
SSH is very powerful and containers many more features than other technologies such as telnet, most people believe SSH is a simple remote command line interface but it also supports techniques such as tunneling, this is the process of directing network traffic from one computer to another using the SSH technology. An example of this technology is the ability to forward internet browser traffic, you browse to a website but the website request is passed through the SSH connection and the computer on the other side makes the request and passes back the response, as the request was performed by the remote computer, it is the IP address of the remote computer which is seen by the internet hiding your identity.
There’s also the ability to run a application on the remote machine and use a technology called x11 forwarding to send the application to your computer, the software appears to be running on your computer but it is really located on the remote machine.
How does it work?
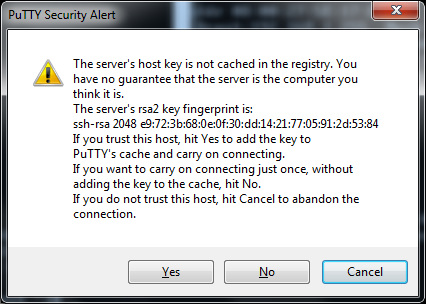
For this technology to work there is a client and a server, the server is located on the remote computer the one which you wish to connect to, and the client is installed on your computer which allows us to connect the SSH server on the remote computer. For security reasons when we first connect to a SSH server the server responds with a key, this key is randomly generated when you install the SSH server and you must write down this key on installation.
Here is an image from my SSH client when I try to connect to a SSH server, the server has responded with a fingerprint key, I now check this key against the key I write down on installation if it is the same then I am connecting to the remote machine directly, if not then there is the possibility I am connecting to the wrong machine or someone has setup a middleman connection with the intent of monitoring the data transfer, if this occurs and you are sure you are attempting to connect to the correct IP address stop all connections immediately and consult your server admin team for guidance.